Phishing Is a Broad Term That Describes
The primary target in the latter classification is. Spear phishing is a term used to describe attacks that are custom-made to the individual being targeted.

Spear Phishing Vs Phishing Key Differences And Similarities Toolbox It Security
The information is then used to access important accounts and can result in identity theft and.
. False A network with a computer dependent on a server is called a clientserver network. Cybercrime encircles the criminal acts that involve computers and networks. Is a broad term that describes any program that is intended to cause harm or convey information to others without the.
And 2 a computer crime that is facilitated by a computer network or device. The attackers often disguise themselves as a trustworthy entity and make contact with their target via email social media phone calls often called vishing for voice-phishing and even text. Specific type of virus.
For example a hacker might send a fraudulent text about a discount on new hardcover book releases if the end user is an avid reader. The term phishing was first used in reference to a program developed by a Pennsylvania teen known as AOHell. For instance an attacker may send email appearing to be from a reputable credit card company or financial institution that requests account information often suggesting that there is a problem.
Phishing is a broader term for any attempt to trick victims into sharing sensitive information such as passwords usernames and credit card details for malicious reasons. Software that is designed to cause damage to or manipulate a computer server client or computer network. Phishing is a broad term that describes any program that is designed to cause harm or transmit information to others without the computer owners permission.
This software spawned other automated phishing software such as the one later used by the Warez community. The program used a credit-card-stealing and password-cracking mechanism which was used to cause trouble for AOL. Social engineering is a broad term that describes tricking people to give out their personal information and gain access to their accounts.
Phishing attacks use email or malicious websites to solicit personal information by posing as a trustworthy organization. Phishing refers to any attack that asks for money or otherwise valuable information account numbers passwords etc. Phishing is the use of convincing-looking emails and web pages to lure you into typing your account numbers and passwords or PINs.
A broad term that describes any program that is intended to cause harm or convey information to others without the owners permission. Phishing is a popular and effective form of social engineering. Phishing is a cybercrime in which a target or targets are contacted by email telephone or text message by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information banking and credit card details and passwords.
Words like malware phishing or encryption can sound like a foreign language to some but theyre important terms when it comes. The goal is to either trick you into providing sensitive personal information like social security number bank account info credit card numbers login usernames and. Phishing is a type of social engineering where an attacker sends a fraudulent eg spoofed fake or otherwise deceptive message designed to trick a person into revealing sensitive information to the attacker or to deploy malicious software on the victims infrastructure like ransomware.
The practice of sending email messages to customers or potential customers of legitimate website asking them to click a link in the email message which usually leads to a spoofed site. 1 computer crimes that target networks or devices directly. Phishing is the term used to identify an identity theft scam designed to target unsuspecting users of electronic communication methods specifically email and text messages and trick them into giving up sensitive personal or business information that can be used to steal their identity raid their bank accounts and more.
A spear phishing attack is one that uses your information to get it eg an impersonation of your friend or spouse. False- Specifications Technical information about hardware components on a computer are called configurations. Often distributed through phishing emails malware implants itself into a computer when a link is clicked or an attachment is opened.
Phishing is a broad term used to describe social engineering techniques that use emails with bogus links to sites youre likely to trust and bogus websites filled with malware-triggering links. Social media is another way that criminals. Internet security is a very broad term that describes protecting private information exchanged over the Internet but there are numerous terms under its umbrella that anyone who uses the Internet should know about.
Often in the form of fake PayPal warning messages or phony bank login screens phishing attacks can be convincing to anyone who is not trained to watch for the subtle clues. Phishing is a broad term that describes any program that is designed to cause harm or transmit information to others without the computer owners permission. Computer crime encompasses a wide range of illegal activities.
Is a broad term that describes any program that is intended to cause harm or convey information to others without the owners permission. However in general the field may be subdivided into one of two types of categories. Thus Cybercrime is a broad term that describes everything from electronic hacking to denial-of-service attacks that.
Software installed with another program that generates advertising revenue for then programs creator by displaying targeted ads to the programs user.

More Ram Can Also Make Some Applications Perform Better In General Computerterms Ihscomputers Ram Multit Structured Cabling Pc Repair Random Access Memory

How To Stop Phishing Attacks The Best Tools To Stop Phishing Scams

Un Informatico En El Lado Del Mal Malware Computer Security Best Hacking Tools Hacking Computer

How To Spot A Phishing Email Using Headers Esilo Data Backup
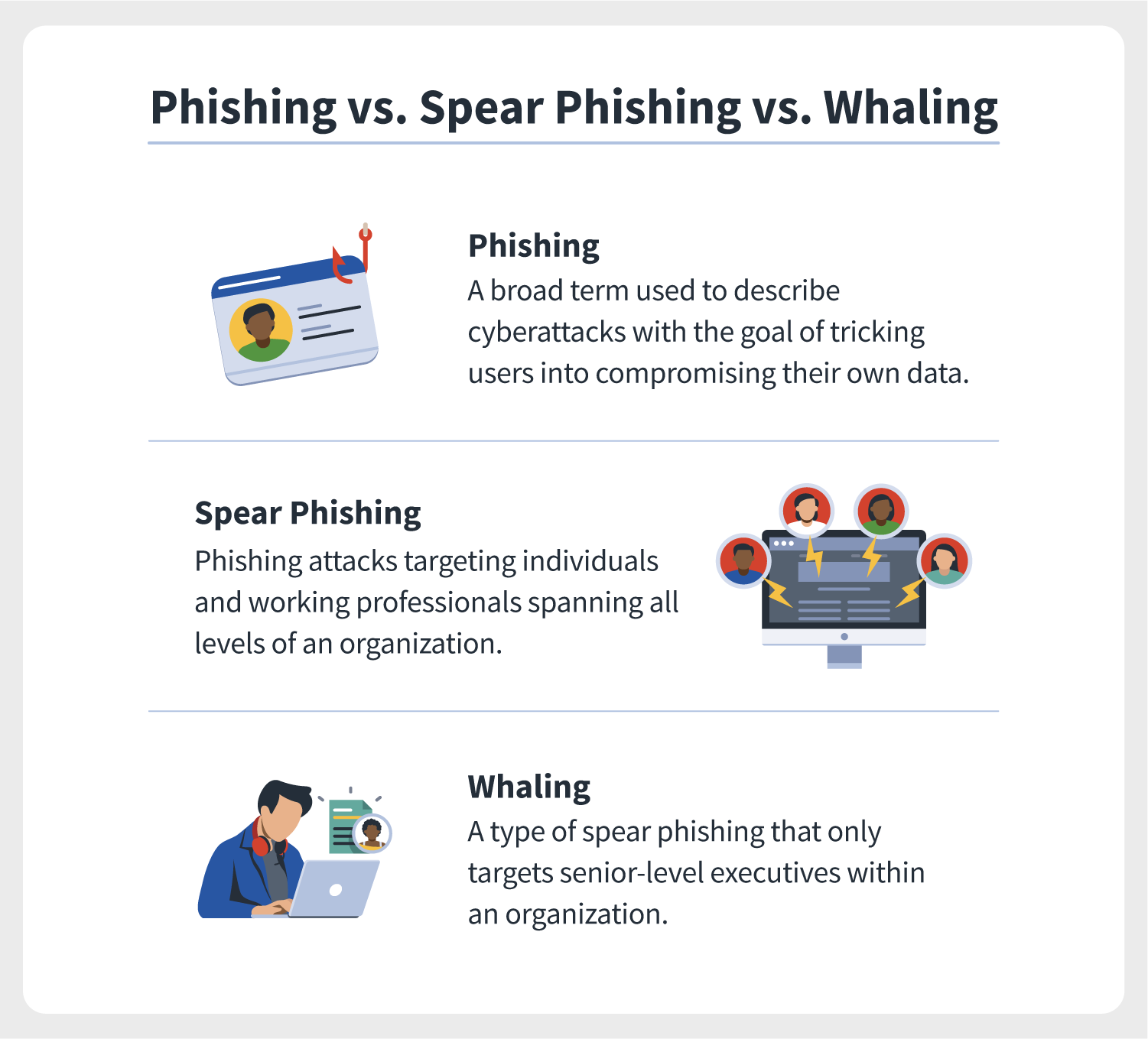
What Is A Whaling Attack Norton
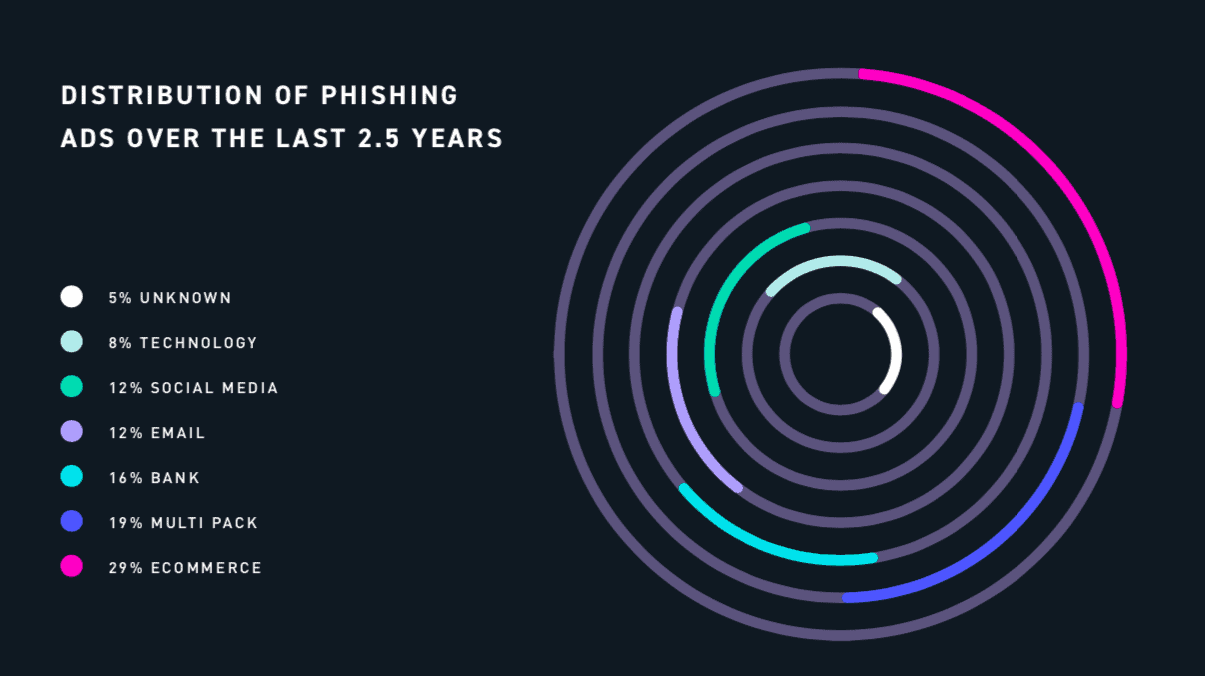
The Ecosystem Of Phishing From Minnows To Marlins Digital Shadows
Spear Phishing Vs Phishing The Differences And Examples Valimail
What Are The Different Types Of Phishing

What Are The Different Types Of Phishing

How To Spot A Phishing Email Abnormal
Spearphising Vs Phishing Vs Whaling What S The Difference

What Is Phishing Phishing Attack Examples And Definition Cisco Cisco
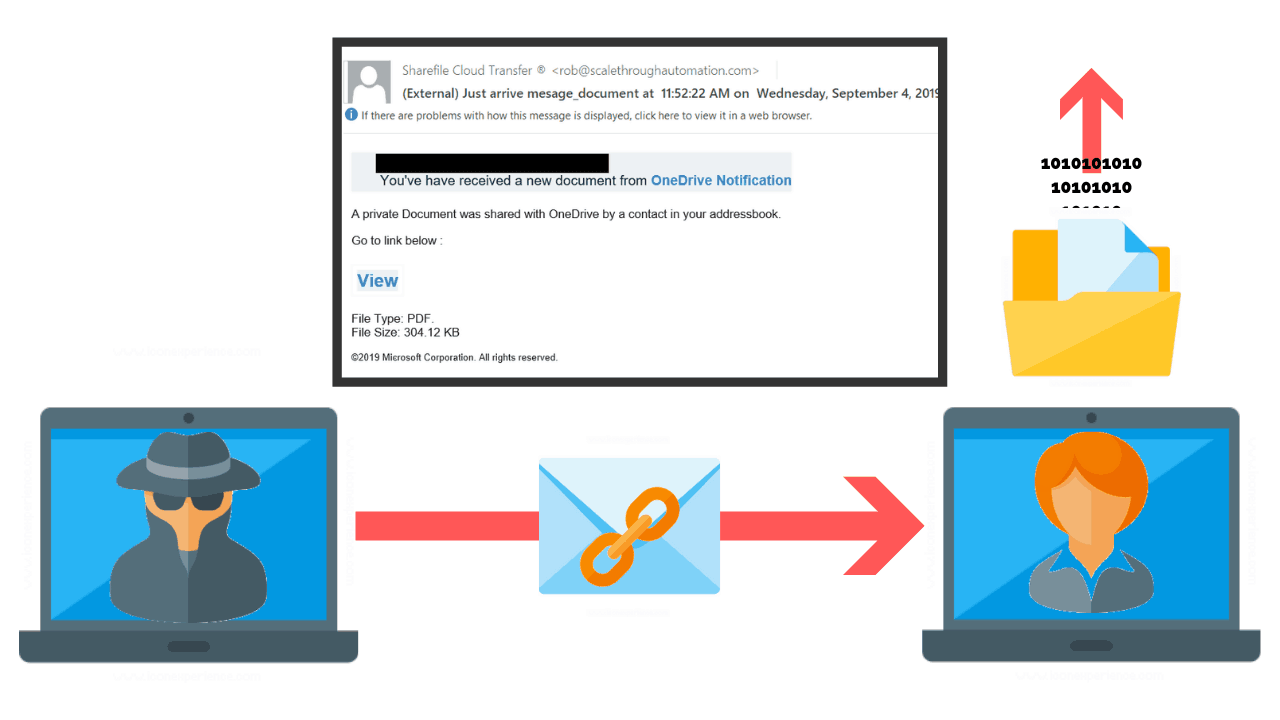
What Is A Phishing Attack And How To Prevent Them Purplesec

Social Engineering Cyber Security Website Cyber Security Website Cyber Security Engineering Social

Understanding Phishing Attacks And Avoiding Them

Image Result For Dyre Banking Malware Statistics Social Media Infographic Social Media Safe Money

What Is Phishing Threat Types Scams Attacks Prevention Phishprotection Com


Comments
Post a Comment